Robust, low‑cost security on untrusted storage infrastructure
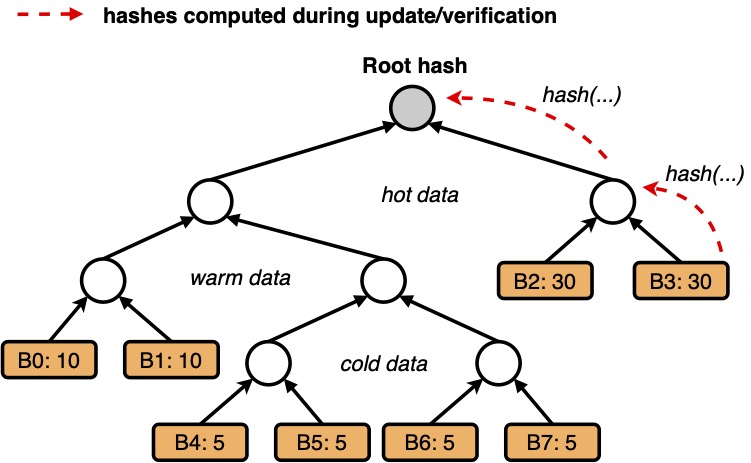
Ensuring the integrity of data stored in the cloud is an important element of cloud security, but it requires executing complex cryptographic checks on data whenever it is read from or written to storage. These checks can degrade storage performance by up to 90%, rendering the performance capabilities of modern storage devices (e.g., NVMe SSDs) useless and creating a strong economic incentive for storage administrators to disable protections in practice. My work was the first to quantitatively explain why these overheads occur in modern settings: CPU hashing speeds are the bottleneck (previously hidden by slower disk speeds), overheads increase non‑linearly, and the underlying integrity data structures are static.
Building on this analysis, I designed an optimal data structure that establishes a lower bound on integrity cost for a given workload profile, then built a new adaptive structure that learns on the fly (without a priori knowledge) and performs near‑optimally across small‑ and large‑scale storage. In complementary work, I formalized secure deferral of verification by coupling asynchronous execution to simple commit and admission rules tied to durability, which moves integrity work off the critical path while remaining hardware anchored and crash consistent, delivering robust integrity protections at near‑zero cost.
Key result:
- This work provided both theoretical and empirical evidence contradicting conventional wisdom about what data structures are necessary and sufficient to protect storage integrity at low cost. It also established a new principled design recipe for systems security researchers demonstrating how to push system optimizations to their limits while remaining within strict security requirements.
Selected publications:
- Quinn Burke, Ryan Sheatsley, Yohan Beugin, Eric Pauley, Owen Hines, Michael Swift, and Patrick McDaniel. "Efficient Storage Integrity in Adversarial Settings." IEEE Symposium on Security and Privacy (S&P), 2025. [PDF]
- Quinn Burke, Ryan Sheatsley, Rachel King, Owen Hines, Michael Swift, and Patrick McDaniel. "On Scalable Integrity Checking For Secure Cloud Disks." USENIX Conference on File and Storage Technologies (FAST), 2025. [PDF]
- Quinn Burke, Yohan Beugin, Blaine Hoak, Rachel King, Eric Pauley, Ryan Sheatsley, Mingli Yu, Ting He, Thomas La Porta, and Patrick McDaniel. "Securing Cloud File Systems with Trusted Execution." IEEE Transactions on Dependable and Secure Computing (TDSC), 2024. [PDF]
Network security in the modern cloud
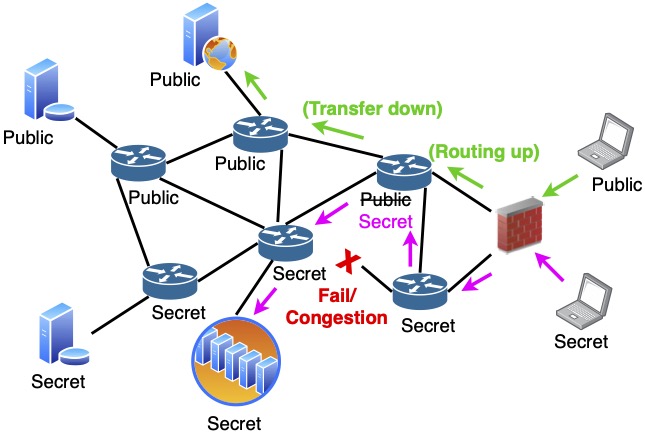
Modern cloud networks increasingly rely on software‑defined networking (SDN), whose programmability enables flexible control but also creates new security challenges. I have leveraged SDN programmability to enforce secure information‑flow policies directly in the routing fabric (at every hop), mitigating configuration errors and limiting attacker lateral movement when endpoint rules are misconfigured or bypassed.
I have also examined vulnerabilities arising from SDN’s control–data plane separation, showing how strategic manipulations of inputs to SDN controllers (e.g., traffic load reports from switches) can mislead load balancers and degrade availability while evading state of the art detection mechanisms. Moreover, I have contributed to analyzing side channels in SDN data planes. These works have produced insights that have informed the design of new defenses for SDN control and data planes.
Key result:
- My work embedding secure information flow policies in the routing fabric shifted policy enforcement from endpoints into the routing fabric, providing verifiable, hop‑by‑hop information‑flow guarantees that provably prevent lateral movement and data exfiltration attacks.
Selected publications:
- Quinn Burke, Fidan Mehmeti, Rahul George, Trent Jaeger, Thomas La Porta, and Patrick McDaniel. "Enforcing Multilevel Security Policies in Unstable Networks." IEEE Transactions on Network and Service Management (TNSM), 2022. [PDF]
- Mingli Yu, Tian Xie, Ting He, Patrick McDaniel, and Quinn Burke. "Flow Table Security in SDN: Adversarial Reconnaissance and Intelligent Attacks." IEEE/ACM Transactions on Networking (TON), 2021. [PDF]
- Quinn Burke, Patrick McDaniel, Thomas La Porta, Mingli Yu, and Ting He. "Misreporting Attacks in Software‑Defined Networking." International Conference on Security and Privacy in Communication Networks (SecureComm), 2020. [PDF]
Other collaborative work
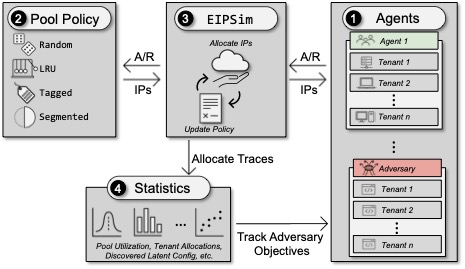
Beyond storage and networking, I collaborate widely across systems security: securing cloud IP address allocation, privacy‑preserving smart cameras, hardware‑assisted binary analysis, and intrusion detection with emerging hardware, among other areas.
Selected publications:
- Eric Pauley, Kyle Domico, Blaine Hoak, Ryan Sheatsley, Quinn Burke, Yohan Beugin, Engin Kirda, and Patrick McDaniel. "EIPSIM: Modeling Secure IP Address Allocation at Cloud Scale." Network and Distributed System Security Symposium (NDSS), 2025. [PDF]
- Yohan Beugin, Quinn Burke, Blaine Hoak, Ryan Sheatsley, Eric Pauley, Gang Tan, Syed Rafiul Hussain, and Patrick McDaniel. "Building a Privacy‑Preserving Smart Camera System." Privacy Enhancing Technologies Symposium (PETS), 2022. [PDF]
- Changyu Zhao, Yohan Beugin, Jean‑Charles Noirot Ferrand, Quinn Burke, Guancheng Li, and Patrick McDaniel. "LibIHT: A Hardware‑Based Approach to Efficient and Evasion‑Resistant Dynamic Binary Analysis." Workshop on Software Understanding and Reverse Engineering (SURE) @ ACM CCS, 2025. [PDF]